Protect your paycheck: Stay ahead of advanced direct deposit scams
Share This Article

How fraudsters are upping their game
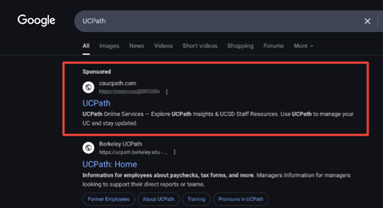
Imagine: You want to check something in UCPath, so you do a quick Google search. You click the top search result for UCPath, not realizing it’s a malicious ad. When you enter your credentials, you share your login information with a fake portal. Once an attacker has your username and password, they modify your direct deposit details and reroute your paycheck to an untraceable account. Even if the fraudulent website is taken down, it may not be detected until real harm is done.
Online threats to your security have become more sophisticated. Attackers are using new, very convincing tactics in attempts to redirect UC employees’ paychecks to their own accounts. Here’s a screenshot of a real ad that UC cybersecurity teams worked to take down recently:
To protect yourself from these threats, it’s critical that you take proactive steps to safeguard your accounts and personal information.
New attack tactics: What makes these threats more dangerous
We’ve all received emails and texts that are clearly suspicious. Filled with errors and misspellings, these messages from unfamiliar senders make outrageous requests. Unfortunately, scammers are getting better.
Here are a few real recent examples:
Malicious search ads: Scammers pay for ads for terms like “UCPath” to lead users to counterfeit login pages that visually mimic the real UCPath portal (see the image above) to steal usernames and passwords.
Masquerading domains: Scammers buy URLs that resemble official UC domains — often only slightly altered — and use them to deceive users who aren’t paying close attention.
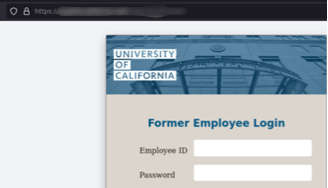
Lookalike websites: Scammers replicate official UC websites using our logos, colors, and photography to create convincing fakes that trick users into sharing credentials.
Convincing phishing emails and fraudulent calls and texts: Advanced phishing emails and fake “Help Desk” phone calls or texts use details like internal UC terminology or branding to appear legitimate.
Duo push fatigue: Scammers send repeated unauthorized Duo MFA push requests until a user mistakenly approves access.
Take these steps now to protect yourself
You’re busy and your inbox is overflowing — but taking just a few seconds to verify links and login pages can be the difference between a paycheck safely deposited in your bank account and a paycheck stolen by scammers.
- Always bookmark the UCPath website (ucpath.universityofcalifornia.edu), access it via the UCnet homepage or type the URL directly.
- Before logging into any website, double-check the URL and page design. For example, look for “universityofcalifornia.edu,” instead of a URL ending with [dot]com or [dot]org.
- Never share your credentials or Duo codes.
- Do not approve Duo pushes you didn’t initiate.
- Submit a report immediately to your local cybersecurity team if anything feels off — no concern is too small.
- Consider enabling free Experian identity monitoring.
What UC is doing now
- Takedown campaigns: Over 15 fraudulent sites have been taken down or are pending removal.
- Manual review and alerts: UC has a process for manually verifying direct deposit changes to some banks, reducing financial losses (but unfortunately not the threat of attack).
- Continuous MFA improvements: UC locations have strengthened Duo protocols to counter push fatigue.
- Search engine monitoring: UC is working with providers to detect and take down malicious ads.
- Task force: A cross-functional, cross-location task force is exploring near- and mid-term technology solutions that will help UC stay ahead of scammers.
The sophistication of these attacks means they can happen to anyone — even tech-savvy users. Your best defense is to stay informed, follow safe login habits and report anything unusual. Your alertness helps protect not just you, but all of UC.
Quick links
- Managing your UC benefits:
- UCPath (health and welfare benefits): https://ucpath.universityofcalifornia.edu
- UC Retirement at Your Service or UCRAYS (UC Retirement Plan benefits): https://retirementatyourservice.ucop.edu
- NetBenefits (UC Retirement Savings Program accounts): https://nb.fidelity.com
- Experian identity monitoring: https://experian.myfinancialexpert.com/login
